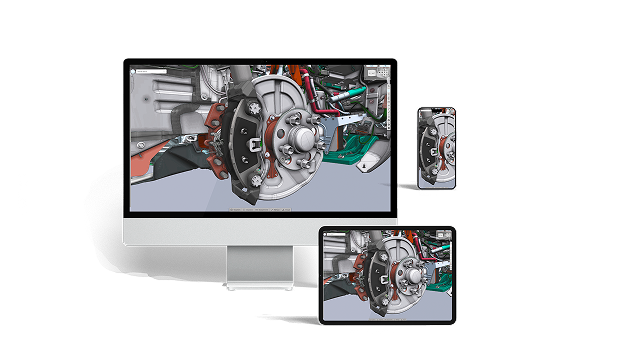
Visualisation with built-in security
Secure 3D CAD collaboration without sending files
instant3Dhub enables organizations to visualize, share, and collaborate on complex 3D CAD data securely and efficiently. We deliver privacy-compliant 3D streaming solutions used by leading engineering organizations worldwide.
.png)
Security and Compliance at Enterprise Scale
Designed to meet global security and compliance standards, instant3Dhub protects your data through encryption, secure access controls, and continuous audits.
TISAX
Threedy aligns with TISAX requirements for information security. Sensitive data and confidential information are protected across processes and systems.
GDPR
Threedy complies with GDPR to protect personal data. Privacy, transparency, and secure data handling are ensured at all times.
Tested and Proven Security
instant3Dhub’s security architecture follows a layered defense approach to protect sensitive engineering data. Each layer – from containerized services to data streaming and access control – is hardened and tested for reliability and compliance.
GDPR
Privacy-compliant by design
Access Control
Role-based and time-limited authorization
Deployment
On-premise, public cloud, or hybrid options
.png)
Secure Access Control
Core Elements of the instant3Dhub Security Architecture
001
Spatial Streaming
instant3Dhub streams only what users need to see. Full CAD files never leave enterprise control. Administrators can define precision, detail, and data depth per project or user.

002
Responsibility Model
Threedy secures the platform architecture; your enterprise governs identity, access, and data policy. Access tokens are scoped and time-bound for complete control.
003
Cloud-Native Security
Containerized services provide isolation, scalability, and encryption. instant3Dhub integrates seamlessly with enterprise IAM and network infrastructure.
%201.png)

Meet Enterprise Privacy and Compliance Requirements
Data Residency
Deploy on-prem, in your cloud, or hybrid, data stays where policy requires.
Secure by Design
Security is embedded into architecture and software development.
Encryption
Data in transit and at rest is encrypted with TLS and managed keys.
Single Sign-On (SSO)
Integrates with existing identity providers for seamless access.
Controlled Access
Scoped tokens define who can see what, for how long, and under which conditions.
Regulatory Compliance
Data sovereignty ensures alignment with regional and regulatory requirements.
Security That Accelerates Collaboration
instant3Dhub enables engineers, suppliers, and partners to collaborate in real time without compromising security.
Request Security Documentation
Get access to instant3Dhub security, architecture, and compliance documentation.
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.